What Does It All Mean?
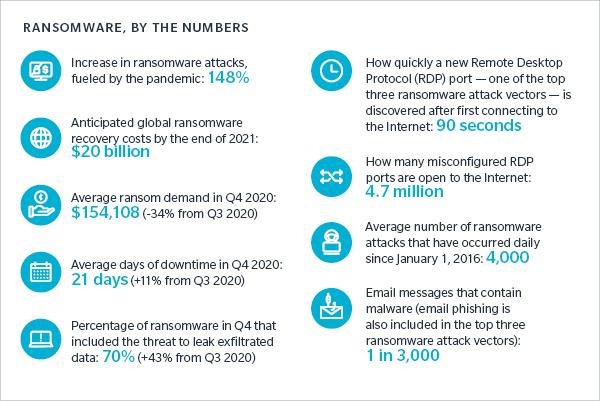
The average ransom demand dropped in Q4 2020. Why? Cyber criminals are increasingly using the threat of data leakage to encourage ransom payments, but not necessarily deleting the exfiltrated data even if the ransom is paid. Ransomware victims are losing trust that their data will be safely deleted, and as such, are refusing to give in to cyber extortion.
While average ransom payment amounts declining is good news for companies, the volume of attacks is still increasing and data exfiltration remains a serious threat. To avoid payment, organizations must be able to effectively restore and recover their data and files—and their networks—from their back-ups or rebuild from scratch!
What Can You Do?
Preparation is key. With the continued threat of data exfiltration and prolonged downtime looming large, we recommend you carefully review your backup strategy. This includes examining what is backed up, where it’s hosted, how often backups occur, and who is responsible and accountable for execution of the back-up strategy. Finally, it is important to exercise and test backup systems regularly.
Cyber insurance should not be overlooked: it can be a valuable tool in the fight against ransomware. Insurance may offer comprehensive coverage for ransom payments, associated costs, and access to vendors and it is also driving organizations to improve their security controls. Certain security controls are starting to be requirements for cyber insurance coverage, namely Multi-Factor Authentication (MFA).
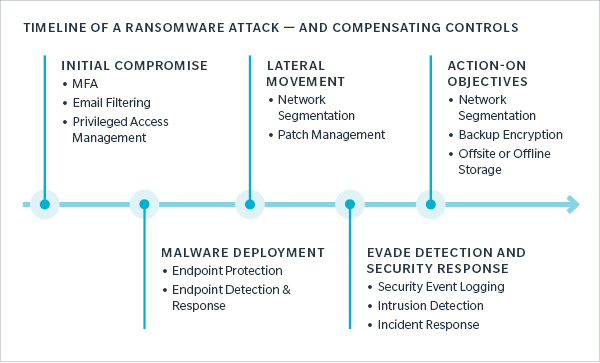
In the fourth quarter, the top three attack vectors for ransomware included email phishing, RDP compromise, and software vulnerabilities. Controls can offer some protection against each attack vector, and at each stage of a ransomware attack. Below is an example of how a ransomware attack may be executed, as well as examples of just a few of the controls that can be helpful at each attack stage.
What Services Can Help Me?
Cyber risk management providers, brokers, and insurers can often provide cost-effective protection and a range of resources and services to help you prepare, respond, recover, and recoup losses from ransomware attacks. This may include:
Preparation:
- Cyber incident response planning and updating
- Evaluation of ransomware preparedness
- Cyber security framework and vulnerability assessments
- Employee training and education
- Cybersecurity best practices
- Cryptocurrency ransom payment support
- Analysis of financial impact
- Vendor identification
Response:
- Secure incident management services
- Vendor identification: including legal counsel, forensic experts, public relations support, and data restoration service providers
- Breach notification services
- Cryptocurrency ransom payment support
- Claims support for insurance recovery
Recovery:
- Event partnership and support, including claims support and advocacy
- Cyber insurance to cover lost revenue, extra expenses, and associated ransomware costs
- Proof of loss preparation and support
- Update/ re-evaluation of incident response plans
Coverage for:
- Lost revenue and extra expenses to continue operations
- Restoration or recreation of corrupted or destroyed data and other intangible assets
- Network or hardware restoration or repair
- Regulatory fines and penalties
- Privacy events
- Reputational harm
